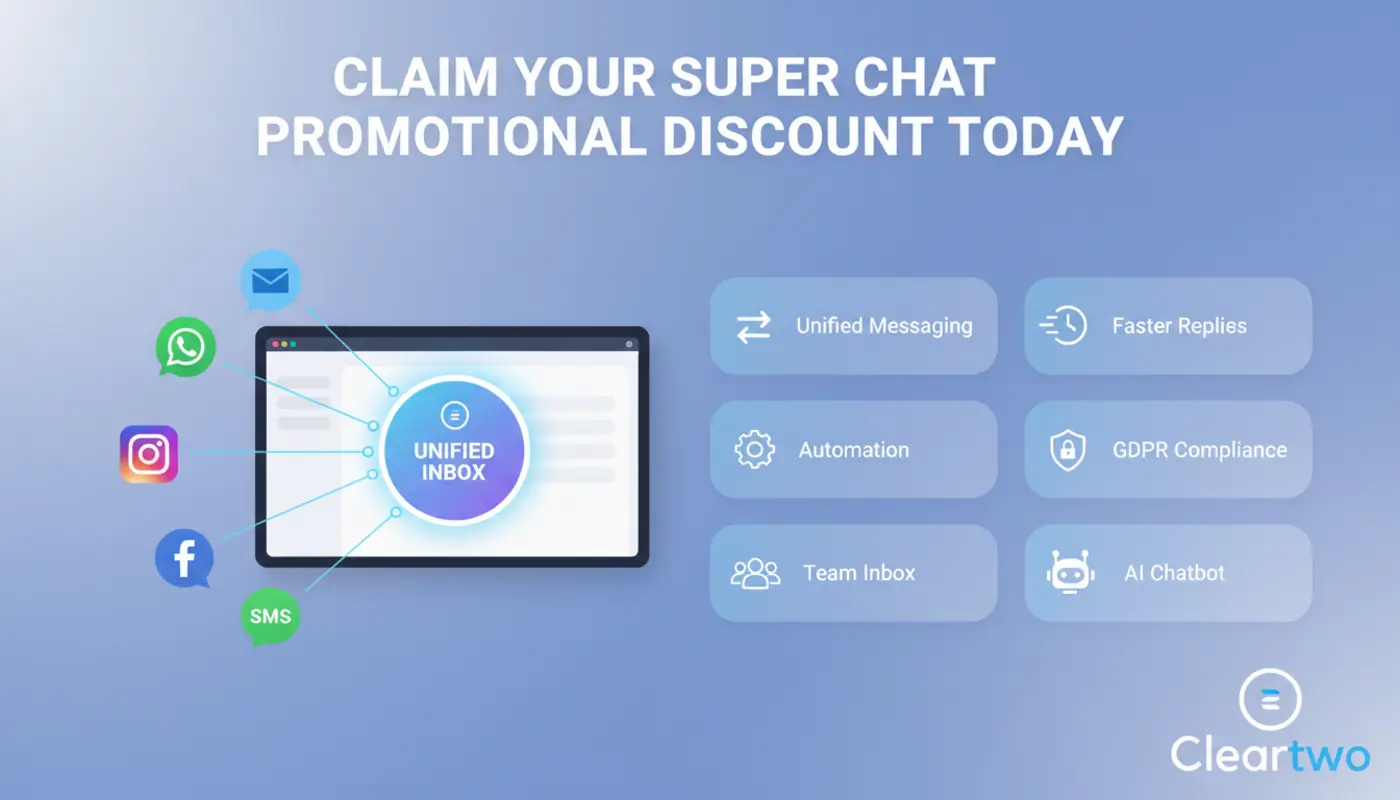
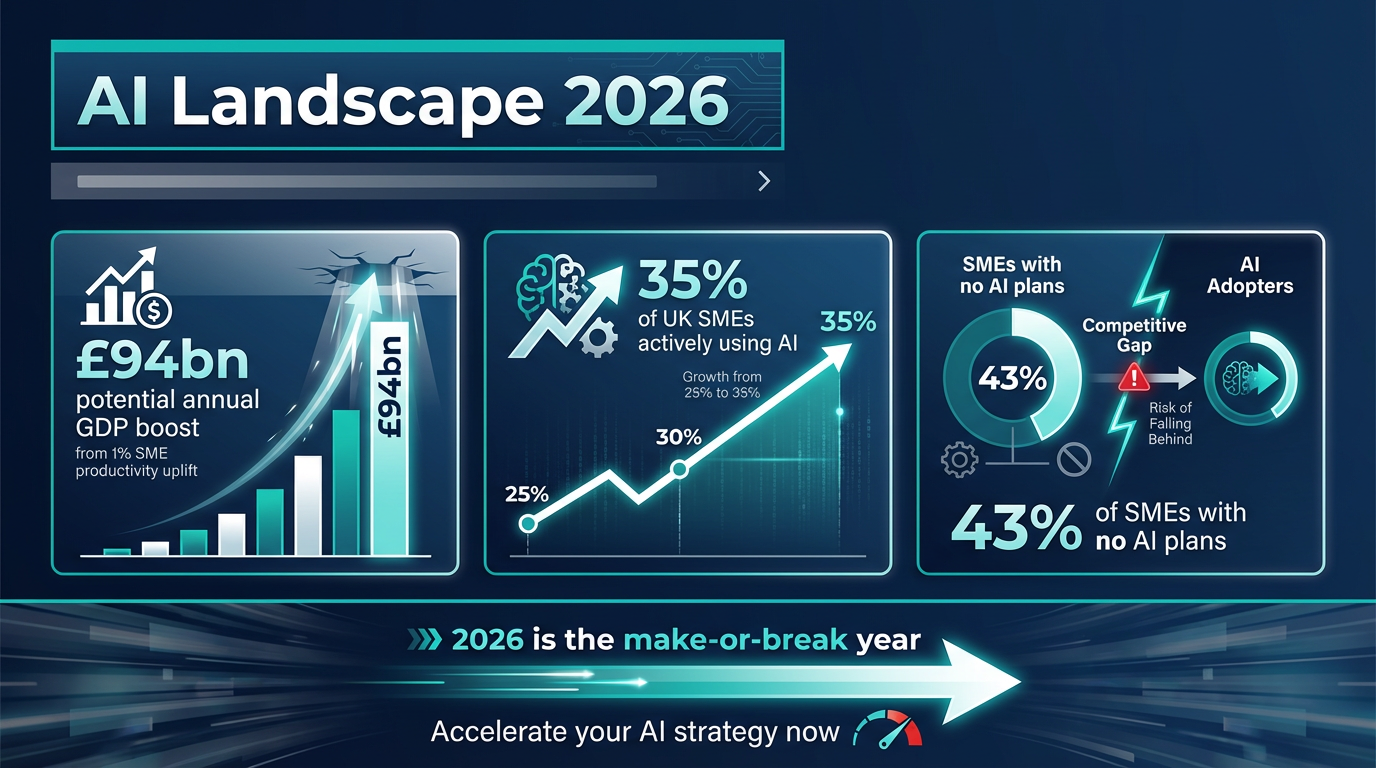
Service
Identity, Access & Security Management

We comply with Microsoft 365 first by protecting the environment. Identity and access are based on empirical best practices and assessment of real business needs. Users work free of exposure to existential barriers. Your data and systems are always secure.
1.
Secure User Identity Management
Users’ identities are managed through a secured cloud and centrally via Azure Entra ID. Access is restricted to subordinates depending on their roles and responsibilities. This is done to mitigate the chances of the case of traitors. Thus, your users receive necessary access only.
2.
Access Control & Permissions
Permissions are custom built to fit into the exact processes of your teams. This eliminates the risk of data exposure and accidental access. Instead of that, users who come in or out of the system are consistently managed. Your space is retained in its original pristine condition.
3.
Security Policies & Compliance
Security policies are the ones you follow to protect your accounts, devices, and data. These policies are in line with the Microsoft compliance frameworks. As such, your organisation is in a better position to efficiently meet regulatory requirements. Security is inherent rather than additional.
4.
Ongoing Monitoring & Risk Reduction
Access and security undergo standstill reviews to cut down on risk. Potential burglars are detected early and are dispensed with before things go awry. Consequently, your organisation runs business as usual, principled and steadfast. Security is like a sneaky hidden guardian which gives you peace of mind.